Ministry of Defense (MoDA) Program Deployment Requirement OPEN AND CONTINUOUS PLACEMENT *Applicants must be current, permanent,
Ministry of Defense Advisors (MoDA) Program Deployment Requirement OPEN AND CONTINUOUS PLACEMENT * Applicants must be current, p
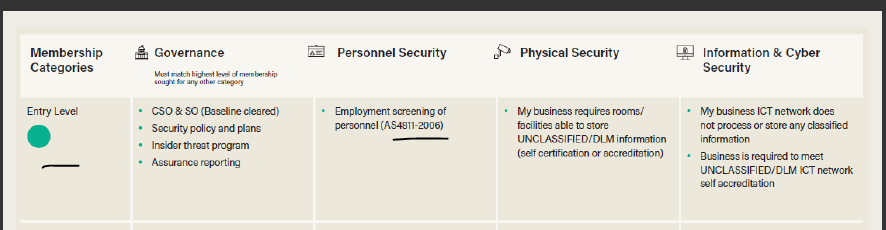
Personnel Security (PERSEC) still remains a challenge for DISP Members • Cleard Life - Trusted & Vetted Workforces - Background Employment Screening Software and Solutions