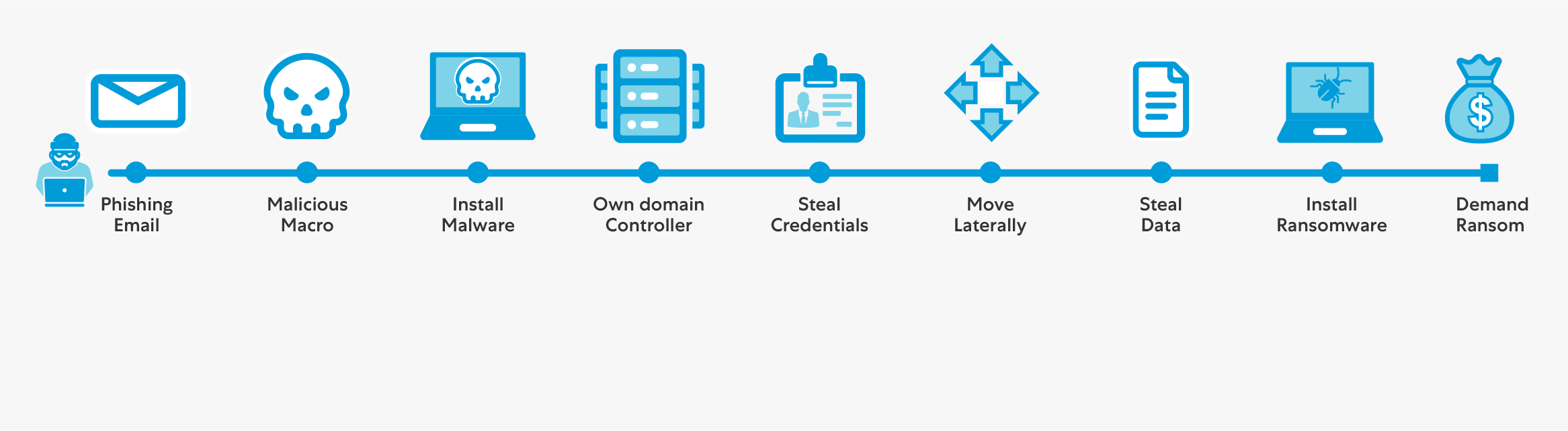
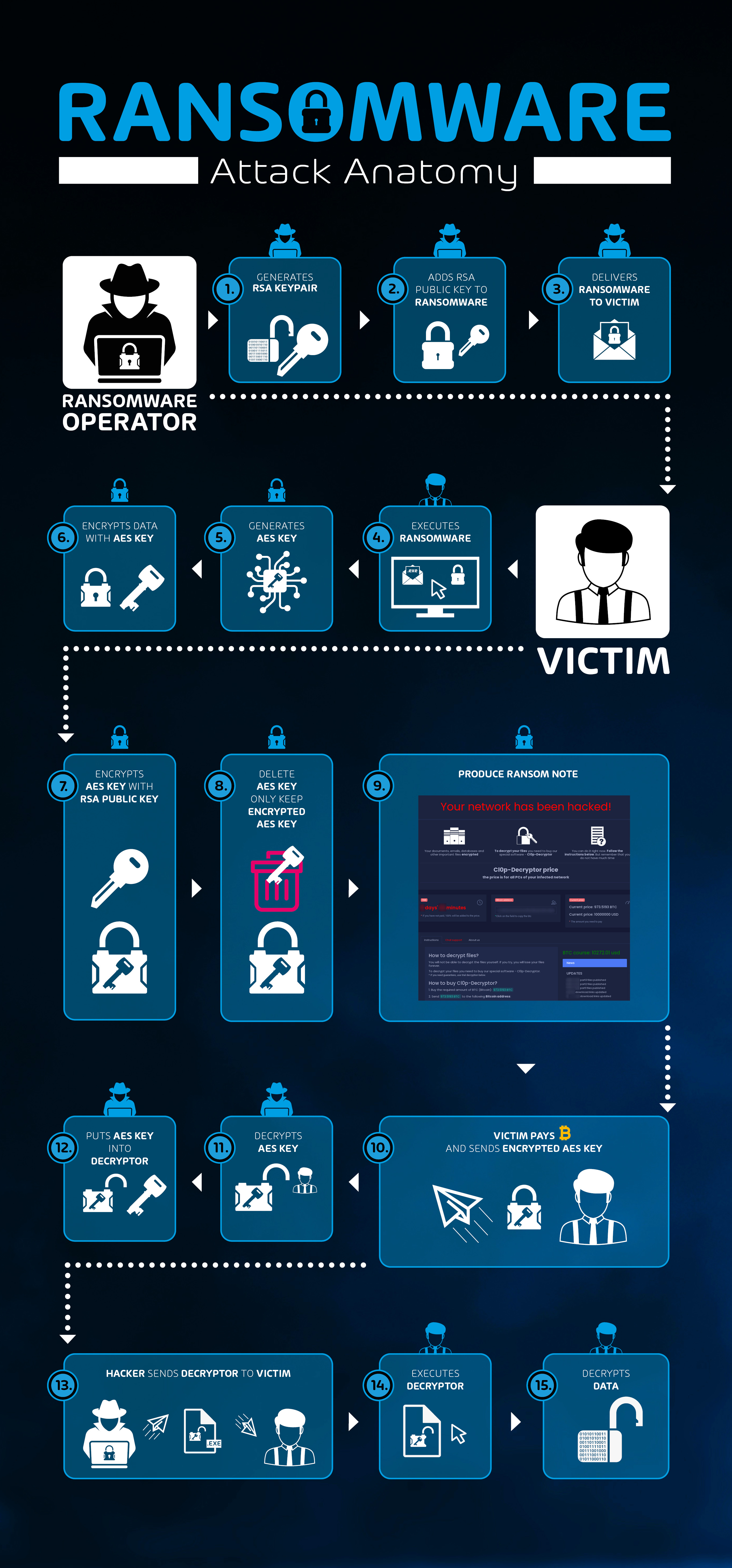
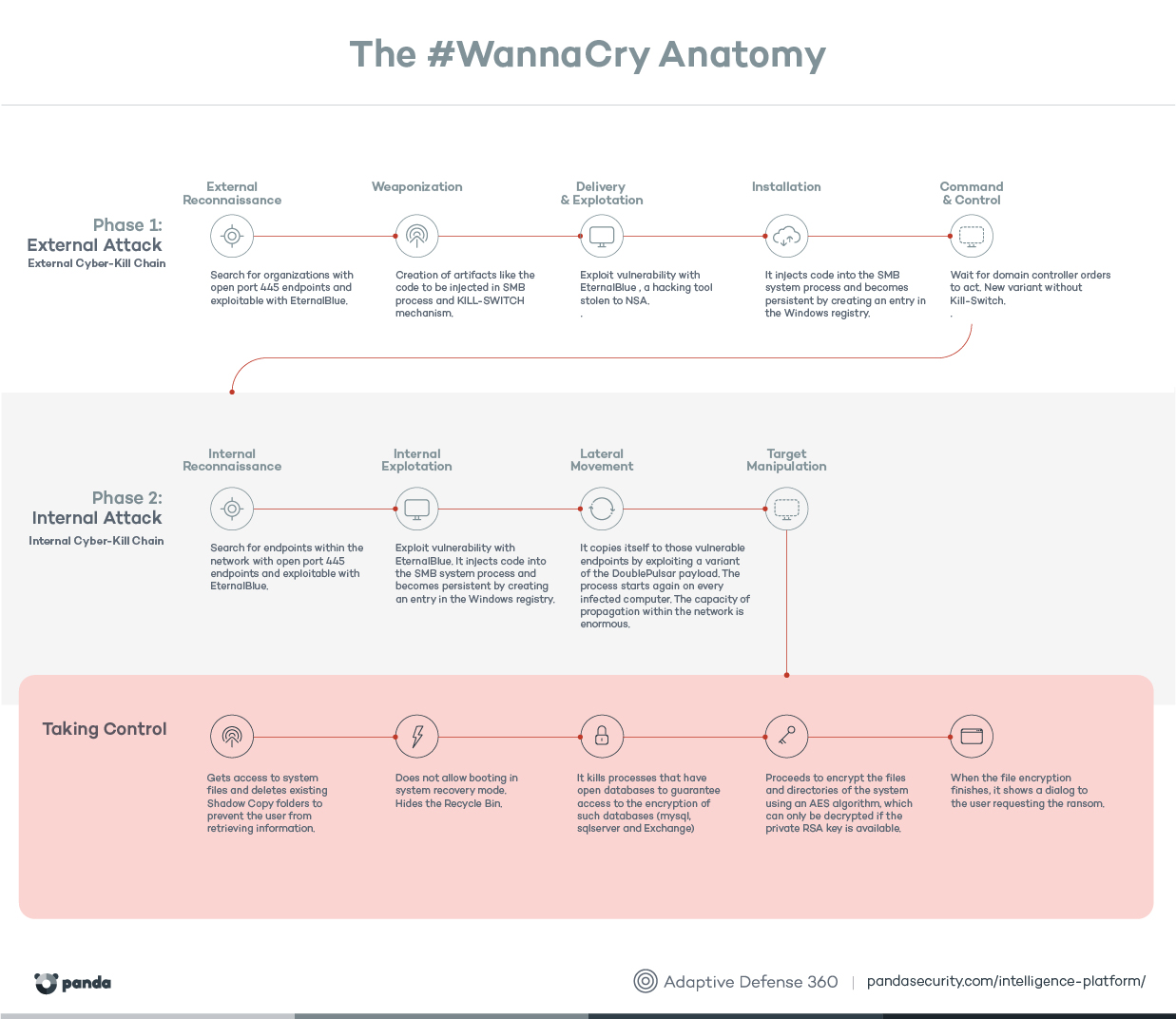
Info-Tech Research Group on Twitter: "Understanding how a ransomware attack unfolds is the key to preventing it effectively. We've created this image that shows the anatomy of a ransomware attack as a

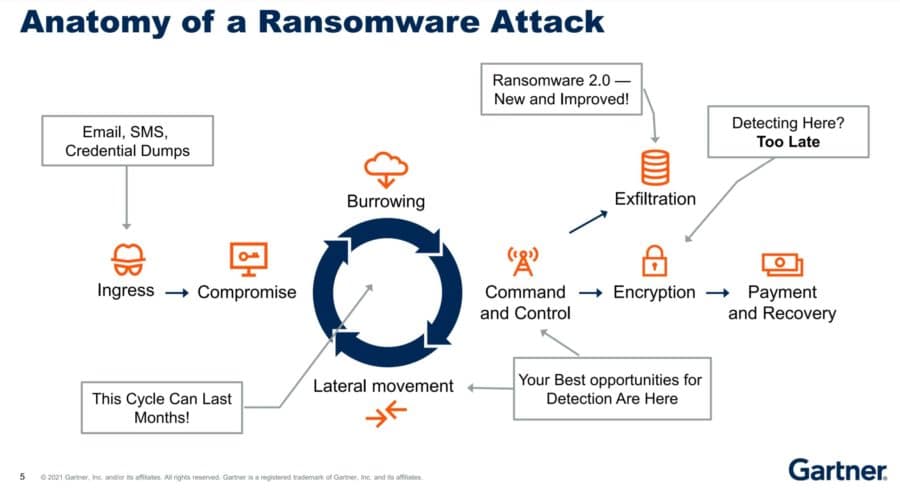
Sophos on Twitter: "How does #ransomware work? We break down the Anatomy of a Crypto-Ransomware Attack: https://t.co/98kBa0rLr3 https://t.co/2zvTPR2KnJ" / Twitter
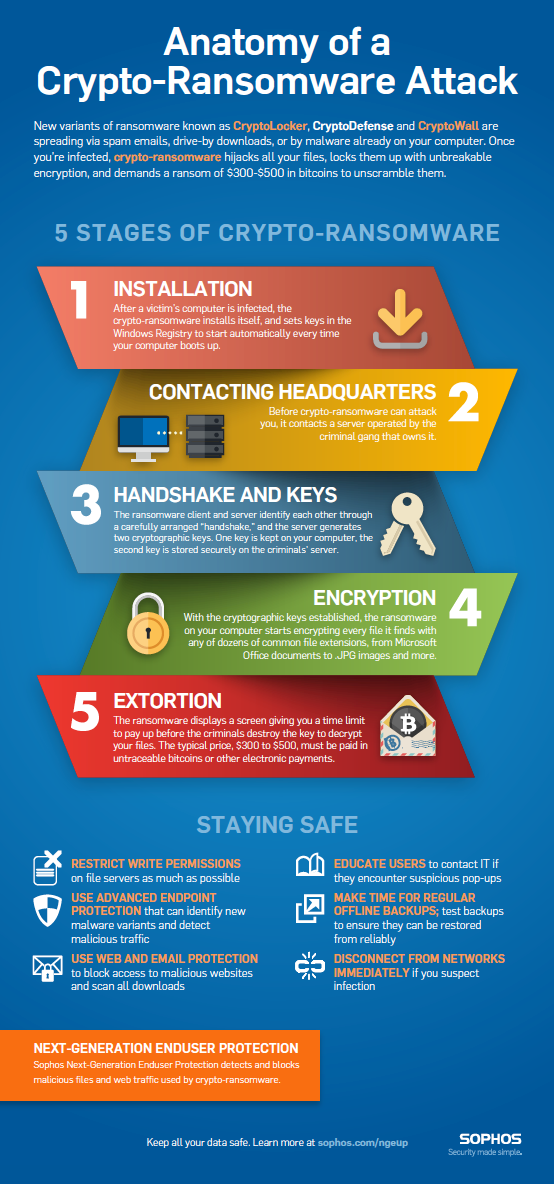
Anatomy of a ransomware attack: CryptoLocker, CryptoWall, and how to stay safe (Infographic) – Sophos News
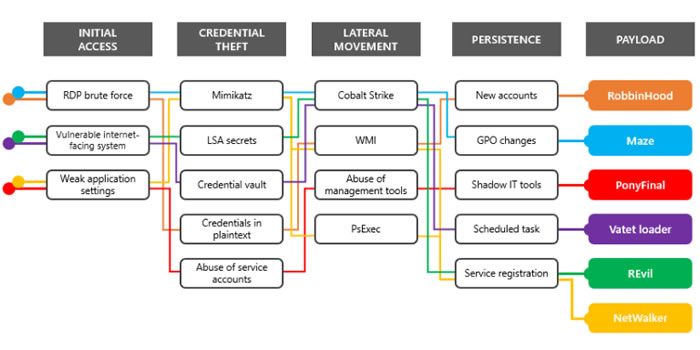


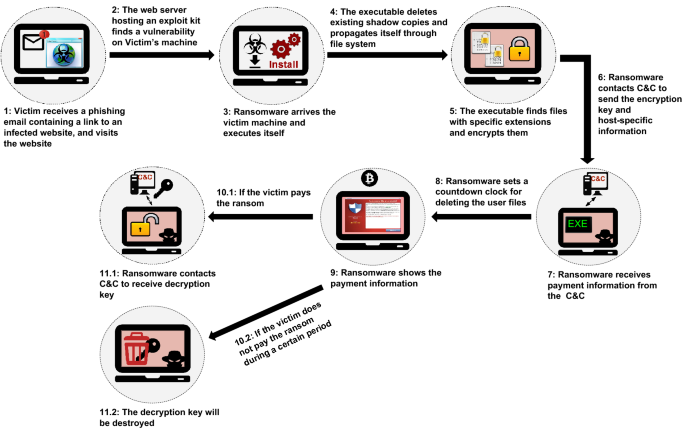



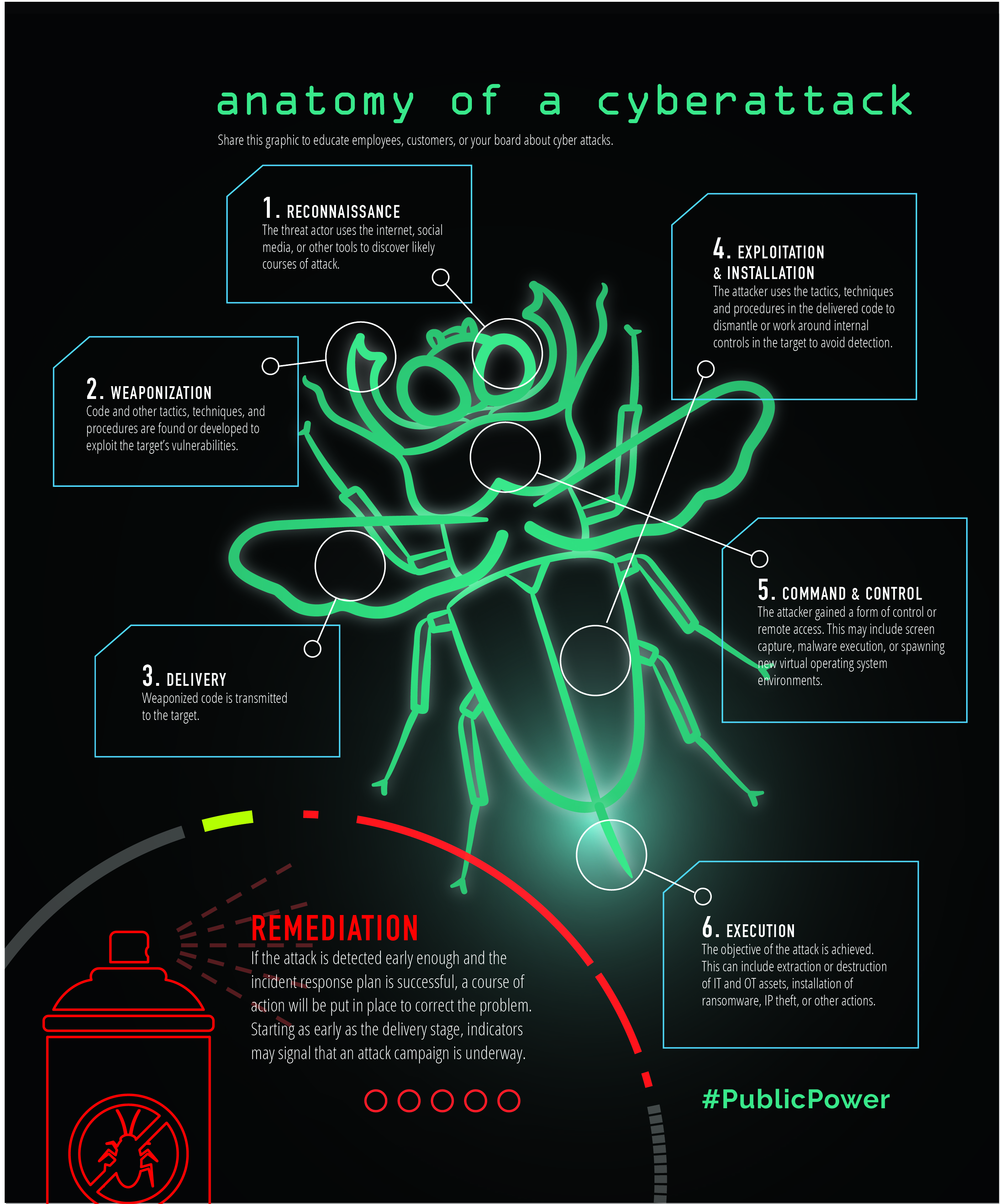
![1: An anatomy of ransomware attacks [8, 15]. | Download Scientific Diagram 1: An anatomy of ransomware attacks [8, 15]. | Download Scientific Diagram](https://www.researchgate.net/profile/Baris-Celiktas/publication/326191046/figure/fig8/AS:644761547468800@1530734540208/An-anatomy-of-ransomware-attacks-8-15.png)