Union Systems Announces Partnership with Daon to Transform Cross-Channel Customer Authentication and Onboarding in Africa | TechCabal

Mixing Forms and Token Authentication in a single ASP.NET Application (the Details) | leastprivilege.com
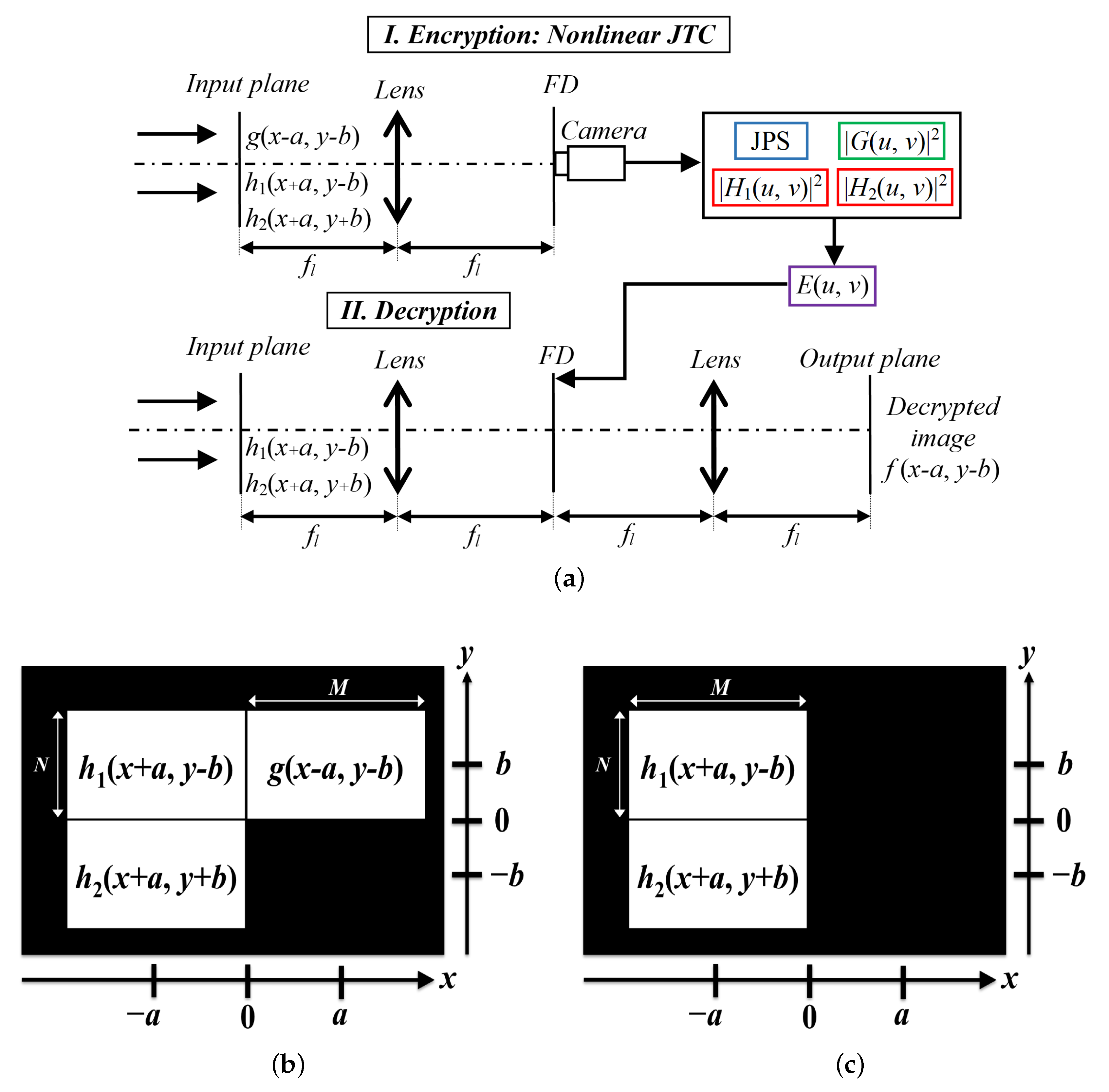
Photonics | Free Full-Text | Image Encryption System Based on a Nonlinear Joint Transform Correlator for the Simultaneous Authentication of Two Users